Picture having one master key that unlocks your entire digital world. That’s the simple idea behind a unified global unified login, more commonly known as Single Sign-On (SSO). Instead of trying to remember dozens of different passwords for your email, streaming accounts, and work apps, you just use one secure login to get into everything.
Your Digital Master Key Explained

Think about your online life like a huge house with tons of locked doors. Every app, website, or service is a different room, and each one needs its own specific key. You've got one for your email, another for your bank, and a whole keychain full for social media, streaming, and all your work tools. Juggling all those keys isn't just a hassle—it's a real security headache.
A unified global unified login takes that messy keychain and replaces it with a single, highly secure digital master key. Once you use that one key to prove who you are, all the doors you're allowed to enter swing open. No more unlocking each one, one by one.
This completely changes how we deal with technology. We go from a clunky, frustrating system to something that just works. It’s the difference between fumbling for the right key in the dark and walking smoothly through an open door.
How This Simplifies Your Daily Routine
The "digital master key" idea works just as well at home as it does for a business. For your home, it means managing your Wi-Fi, smart devices, and even entertainment bundles like MyBundle.TV with one login you already trust. Say goodbye to forgotten passwords and endless "reset password" emails.
For a business, the benefits are even bigger. A unified login gives employees instant and secure access to all the tools they need to do their jobs, from the VoIP phone system to managed network services. The impact on day-to-day work is immediate.
- Eliminates Password Fatigue: No more pressure to invent and recall countless complex passwords. This cuts down on the risky habit of using weak or recycled credentials.
- Boosts Productivity: Employees get into their apps right away, saving precious time they’d otherwise waste logging into different systems all day long.
- Strengthens Security: With access managed from one central point, it’s much easier for administrators to enforce strong security rules, like multi-factor authentication, across the board. It also makes cutting off access for a former employee a simple, one-click process.
At its core, a unified global unified login is about building a foundation of trust. Once a central, secure authority verifies your identity, all the other connected services accept that verification and let you in.
This centralized approach isn't just a nice-to-have; it's a modern necessity for managing our increasingly connected lives. The more services and devices we add, the more we need a simple, secure way to access them all. To get into the nitty-gritty, you can learn more about the core principles of Single Sign-On in our detailed guide.
The True Benefits For Homes And Businesses

The idea of a "digital master key" is a game-changer, but its real value comes to life when you see how it simplifies your day-to-day. A unified global unified login isn't just a technical term; it delivers real, practical advantages for both your home and your business.
For home users, the biggest win is getting rid of digital headaches. Think about managing your Premier Broadband account—checking a bill, setting up content filters—with one secure sign-on. That same login could then get you into your MyBundle.TV streaming package. No more digging for another password when you just want to sit back and watch a movie.
This kind of simplicity is a quality-of-life upgrade. It makes your digital home run smoother.
A Clear Before And After Picture For Businesses
For a business, the impact of a unified login is even bigger. Just picture the "before" scenario: employees juggling a dozen different logins, and the IT help desk buried in password reset requests. In fact, these tickets can eat up up to 50% of all support calls, wasting time and money.
Onboarding a new employee is a painfully slow back-and-forth of requesting access to one system after another. Every separate login is another weak spot, another potential door for a data breach. And when an employee leaves, it’s a mad scramble to shut down all their access points, hoping you don't miss one.
Now, imagine the "after" with a unified login system:
- Onboarding Transformed: A new team member gets one login that unlocks everything they need from day one—their VoIP phone dashboard, customer portals, and any internal software.
- Productivity Unleashed: Staff can switch between apps without hitting a login wall, saving valuable time throughout the day.
- IT Efficiency: The flood of password reset tickets slows to a trickle, freeing up your IT team for projects that actually grow the business.
This is a real improvement in how your business operates, turning wasted time back into productive work.
Centralized Control Meets Enhanced Security
While convenience is great, the security boost you get from a unified global unified login is the most important benefit. Instead of defending dozens of separate, weaker entry points, you focus all your security efforts on a single, strong one.
A unified login doesn't just simplify access; it strengthens your security posture by giving you a single point of control. Granting or revoking permissions for any user, across every integrated application, becomes a simple, one-click action.
This is critical for any growing company. When an employee changes roles, you can instantly adjust their access to match their new duties. When someone leaves, you can shut down all their access at once, closing potential security holes immediately.
A central system also makes it much easier to roll out stronger security policies, like Multi-Factor Authentication (MFA), across the board. This kind of unified structure is also the backbone for platforms like Unified Communications as a Service (UCaaS), which pull all your communication tools into one easy-to-manage system. You can see exactly how this works by learning more about what UCaaS is and how it benefits businesses.
At the end of the day, a unified login delivers a clear return. It cuts down on administrative work, boosts employee productivity, and creates a much safer and better experience for everyone.
How Unified Login Technology Really Works
To really get how a unified login works, let's forget the technical jargon for a minute and use a simple analogy.
Picture yourself at a big corporate conference spread across multiple buildings. First, you head to a central registration desk. This desk is your Identity Provider (IdP).
A security guard there checks your ID, verifies you're on the guest list, and hands you an official event pass. This pass is now your trusted credential. With it, you can walk over to any building on the campus—the keynote hall, the cafeteria, or a breakout session—and just flash the pass to the guard at the door.
Each of those buildings is a Service Provider (SP). The guards at their doors don't need to re-check your ID or scan a master list. They trust the main registration desk (the IdP) already did the heavy lifting. They see your official pass and wave you in. That’s the big idea behind a unified global login.
The Key Players in the Process
In this digital handshake, you've got two main roles, just like in our conference analogy. Understanding them is the key to seeing how the whole system stays secure and seamless.
The Identity Provider (IdP): This is the central hub that manages your identity. It's the one place you log in with your username and password. Its only job is to authenticate you—confirm you are who you say you are—and then issue a secure digital token, which is like that event pass.
The Service Provider (SP): This is any app or website you want to get into, like your company's VoIP dashboard or a customer portal. The SP never sees or handles your password. Instead, it has a pre-arranged trust relationship with the IdP. When you try to log in, it simply asks the IdP for your verified token.
This separation of duties is what makes the whole thing so secure. Your password is only ever shared with the highly-secured IdP, not with every single application you use.
The Protocols That Make It Happen
The back-and-forth between the IdP and SP is guided by secure rules called protocols. Think of them as the specific language the security guards use to communicate. The two most common protocols you’ll run into are SAML and OpenID Connect.
Security Assertion Markup Language (SAML) is the go-to in most corporate settings. It’s like the main registration desk sending a sealed, digitally signed envelope to each building guard. This envelope contains a statement, or "assertion," basically saying, "We’ve verified this person, and here’s what you need to know about them."
OpenID Connect (OIDC) is what you usually see in consumer apps, like when you use "Log in with Google" on a new website. This is more like showing your driver's license. The app (SP) sees your trusted ID (issued by an IdP like Google) and accepts it as proof of who you are. OIDC is built on a newer framework called OAuth 2.0 and is generally seen as more modern and lightweight.
The magic of a unified global login is all about established trust. The Service Provider trusts the Identity Provider to handle the tough job of authentication, so it doesn't have to. This trust is what unlocks a smooth and secure experience across dozens of applications.
Let's break down how these two protocols stack up.
Comparing Popular Authentication Protocols
Here's a quick comparison of the two main protocols that power unified login systems, highlighting their primary use cases and strengths.
| Protocol | Stands For | Primary Use Case | Analogy |
|---|---|---|---|
| SAML | Security Assertion Markup Language | Enterprise applications and corporate SSO | A security guard at a corporate campus gives you a pass that all buildings accept. |
| OpenID Connect | OpenID Connect | Consumer-facing applications and mobile logins | Using your government-issued ID to prove your identity at different venues. |
At the end of the day, both protocols get you to the same place: they securely pass your identity verification from one central authority to all the different applications you need to use. This elegant, secure dance is what powers the convenience of a modern unified global login, wiping out password chaos and making your digital life a whole lot simpler.
Putting Unified Login Into Practice
Knowing how a unified global unified login works is one thing, but seeing it in action is where you really grasp its value. This isn't just some backend IT convenience; it makes life smoother and more secure for everyone, from a family managing their internet plan to a business juggling multiple complex operations.
For our residential customers, the benefit is refreshingly simple. Think about your Premier Broadband account. Instead of juggling one password for your billing portal and another for Premier Protects content controls, a unified login gives you a single, secure key to everything. This same idea applies to your entertainment—you can jump into your MyBundle.TV streaming package without trying to remember yet another password. It’s all about removing those small but constant headaches from your digital life.
Unlocking Business Efficiency
For businesses, the practical side of a unified global unified login is even more powerful. It acts like a central nervous system, providing secure, hassle-free access to the tools your team relies on every single day. It turns a collection of separate platforms into one cohesive, manageable system.
Imagine how a unified login changes these common business tasks:
- Hosted VoIP Dashboard: The hub for all your communications—phone lines, call routing, voicemail—becomes instantly accessible. A sales manager can log in once and immediately start setting up call groups without digging around for a separate password.
- Managed Network Edge Controls: This is a huge win for IT admins. One secure login grants them access to the platform controlling network security, monitoring traffic, and managing device policies. No more hopping between different security consoles.
- Customer Portals: Employees can get into the CRM or support portals without a hitch, letting them help clients faster and more effectively instead of getting stuck on a login screen.
This diagram breaks down the simple, secure flow: a user logs in once with their Identity Provider, which then grants them access to all their connected apps.
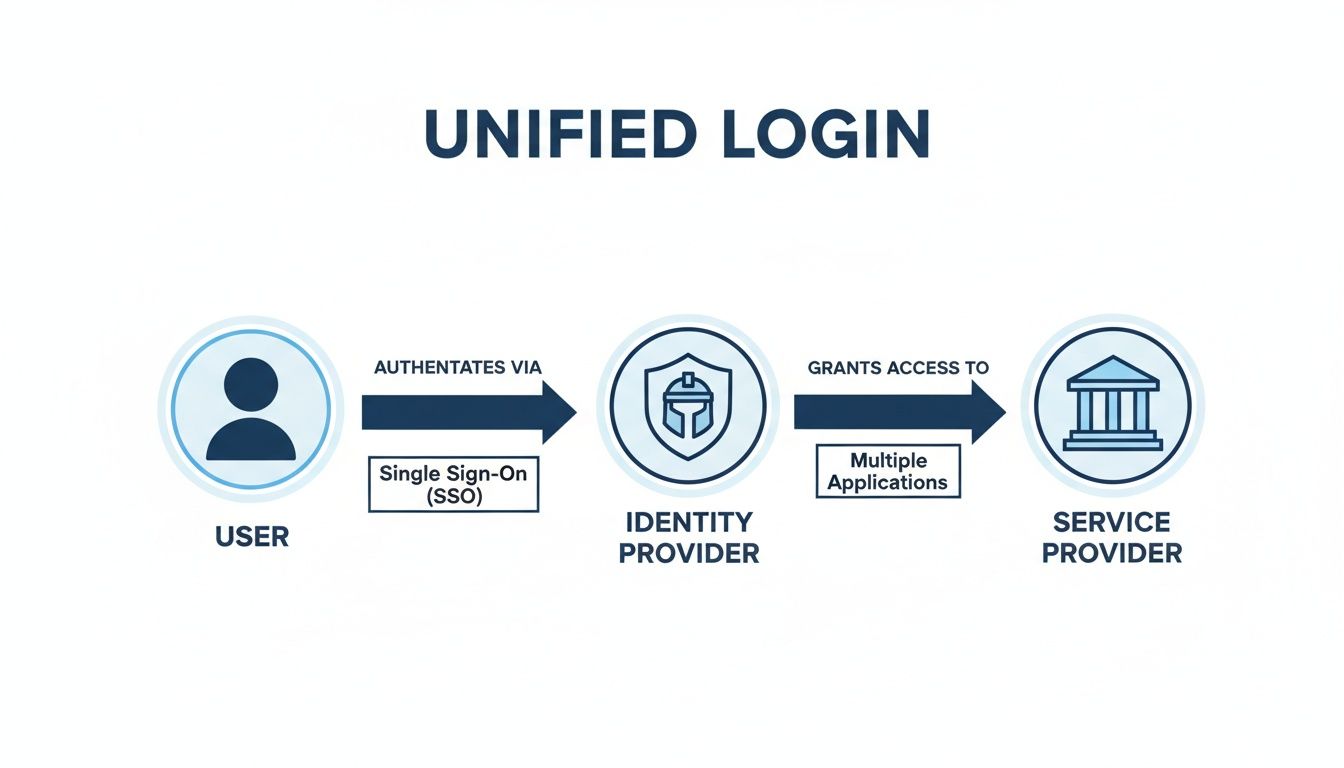
What this really shows is the core concept of trust. The user’s identity is checked just one time by a central authority, which then vouches for them across all the other services.
The Modern Integration Model
The good news is that modern platforms are built for this. Integrating services isn't the complex, custom-coded nightmare it used to be. Today, it all relies on the standardized protocols we've talked about, like SAML and OpenID Connect. This means a service like a Hosted VoIP system is designed from the start to "speak the language" of identity providers.
The goal of modern integration is to build an ecosystem where trust is the default. When a new service is added, it’s simply configured to trust your central Identity Provider, instantly joining the unified login environment without needing a new password for every user.
This approach is built to scale. As your business grows and brings on new software, each application can be folded into your existing unified login framework quickly and securely. It's a key part of smart identity and access management, especially when you bring in tools like Active Directory. You can dive deeper in our guide on how Active Directory Integration streamlines business operations.
Looking beyond general business tools, it’s useful to see how specific industries are innovating. For instance, the future of property management technology shows how these same principles are changing how residents and staff interact with building services. This forward-thinking mindset is becoming the standard everywhere, proving that a unified global unified login is the practical foundation for a secure, productive, and user-friendly digital workplace.
Essential Security And Compliance Strategies

A unified global unified login system is incredibly powerful because it turns countless potential weak spots into a single, fortified entry point. Think of it as replacing a dozen flimsy doors with one bank vault door. But this also means that your "digital master key" has to be guarded with everything you've got.
There’s a common myth that a unified login creates a single point of failure. The reality is just the opposite. A well-secured central system is infinitely better than managing passwords scattered across different services—many of which are weak, reused, or forgotten.
This approach lets you focus all your security efforts on one place. Instead of spreading your defenses thin, you get to build a fortress around the main gate.
Building Your Digital Fortress
Protecting that master key requires layers of defense. No single security measure is a silver bullet. The idea is to create overlapping safeguards that make it incredibly difficult for anyone unauthorized to get in.
These are the absolute must-haves for a secure unified login strategy:
Multi-Factor Authentication (MFA): This is non-negotiable. MFA demands at least two forms of proof before granting access—something you know (a password), something you have (a code on your phone), or something you are (a fingerprint). It’s like needing both a key and a unique passcode to open the vault.
Strong Password Policies: Even with MFA, that first line of defense needs to be solid. A unified system lets you enforce universal rules like minimum length, complexity, and regular password changes across the board. No more weak links.
Regular Security Audits: You can't protect what you don't watch. Regular audits mean checking access logs, reviewing permissions, and scanning for vulnerabilities to fix weaknesses before they become problems. It’s about staying proactive, not just reacting to threats.
A centralized unified login system transforms security from a scattered, reactive chore into a focused, proactive strategy. It gives administrators the power to enforce strong, consistent policies for every single user and application.
A core part of any unified login strategy is knowing how to protect personal information online through these kinds of multi-layered defenses.
Aligning Security With Compliance Mandates
For any business, security isn't just about stopping breaches—it's about meeting strict industry rules and regulations. A properly set up unified global unified login system provides the clear audit trails and access controls you need to prove you're compliant.
The stakes are higher than ever. Since 2021, attacks on workplace platforms have skyrocketed by a shocking 300%, and network downtime can cost a business $5,600 per minute.
A solid SSO solution helps you meet several key compliance standards:
GDPR (General Data Protection Regulation): GDPR requires tight control over who accesses personal data of EU citizens. A unified login gives you precise control to grant, change, or revoke access instantly and generate the detailed reports auditors demand.
HIPAA (Health Insurance Portability and Accountability Act): In healthcare, protecting patient information is paramount. A unified system with MFA and detailed logs ensures only authorized staff can access sensitive health records, which is a core requirement of HIPAA.
By weaving these security and compliance measures together, a unified login becomes more than just a convenience. It becomes a strategic tool that safeguards your data, keeps you compliant, and builds trust with customers. To learn more, check out our guide on the best practices for network security.
Why a Unified Login Is No Longer Optional
In a world packed with digital services and connected devices, the old way of managing access just doesn't cut it anymore. What used to be a small headache—juggling dozens of passwords—is now a major drain on productivity and a serious security risk. The unified global login isn't a luxury for tech experts; it's a basic need for modern life.
This change is happening because our digital world is growing at an incredible rate. There are now 5.78 billion unique mobile users, which is 70.1% of the world's population. In the last year alone, 294 million new users came online, proving that the demand for simple, secure access is exploding everywhere. You can see the full picture of this massive growth in the Digital 2026 Global Overview Report.
This growth has created a messy problem. The more tools we use to make our lives "easier," the more complicated it gets to manage them all. A unified login cuts right through that mess, giving you a single, secure key to your entire digital world.
The Foundation of Modern Digital Life
For both homes and businesses, easy access is the key to being productive and safe online. The days of scattered logins are over. The future is all about a smarter, more connected approach to who gets in and who stays out.
A unified global login is more than just simplifying passwords. It’s about taking back control, boosting your security, and taming the complexity of our hyper-connected lives. It makes technology work for you, not the other way around.
By bringing all your access points together, you build a system that's far easier to manage and much safer than the old, scattered alternative. It’s the difference between organized efficiency and digital chaos.
The Clear Path Forward
Switching to a unified login strategy gets your home or business ready for what's next. It allows you to add new services without a fuss and protects your digital life from new threats. This isn't just about convenience—it's about building a strong, flexible foundation for everything you do online.
Simple, secure access makes life better for everyone:
- For Families: Spend less time dealing with forgotten passwords and more time enjoying your connected entertainment and smart home.
- For Businesses: Get new employees up and running faster, help your team be more productive, and build a stronger defense to protect your company's important data.
As we rely more and more on digital tools, the need for a unified global login is crystal clear. It's the master key that unlocks a simpler, safer, and more productive digital future. Ready to simplify your digital world? It's time to embrace a unified approach to access.
Frequently Asked Questions
Even when you see the clear advantages, it's natural to have a few questions before jumping into a unified global login system. Let's tackle some of the most common things we hear about security, setup, and whether it's really worth it.
Is a Unified Login a Single Point of Failure?
It's a fair question. While you're centralizing access, a unified login system isn't automatically less secure. In fact, it's usually the opposite. When you lock it down with Multi-Factor Authentication (MFA), it becomes vastly more secure than trying to manage dozens of separate, often weak, passwords floating around the web.
Think of it this way: this central model lets your security team set strong, universal rules for everyone. Even better, it gives you a single "off switch." If a threat pops up, you can instantly kill access to all applications at once—a task that’s slow and full of mistakes when you’re dealing with separate logins for every service.
A unified login doesn't create a weak point; it creates a strong point. You're shifting your focus from defending countless backdoors to fortifying one main digital gateway, concentrating your defenses where they count the most.
Can We Integrate Existing Apps?
Absolutely. Modern unified login solutions are built to play nice with others. They rely on standard, widely-used protocols like SAML 2.0 and OpenID Connect, which means they work right out of the box with thousands of popular cloud and SaaS applications.
This ability to connect everything is what makes the user experience so smooth. It means your team can get into their CRM, communication tools, and other business software with just one secure login.
What Is the Difference Between SSO and Federated Identity?
You’ll often hear these terms used together, and while they're related, they describe slightly different ideas that build on each other.
Single Sign-On (SSO): This is all about using one login to get into multiple apps inside a single organization. A perfect example is an employee using their company credentials to open their email, VoIP dashboard, and internal portals.
Federated Identity: This takes the concept a step further by building a bridge of trust between different organizations. It lets a user from Company A use their login to access services from Company B. For instance, using your corporate account to get into a trusted partner’s project management portal—that's federation in action.
Basically, SSO handles unified access within your own walls, while federation extends that same convenience and trust to your partners.
Ready to simplify access and strengthen security for your home or business? Premier Broadband delivers the 100% fiber network and advanced solutions you need for a seamless digital experience. Learn more at https://premierbroadband.com.